Security profile for AT&T

About
Introducing a new user experience that simplifies the process of managing account security settings. With a primary focus on simplicity and a seamless flow, our interface not only enables users to efficiently manage their security but also educates them on essential security practices.
Team
- UX Lead
- Architect Lead
- Product Manager
- Content writer
- Dev OPs
Problem
Create a user-friendly interface that presents security settings clearly, balances security and usability, allows personalization, prevents errors, includes strong authentication and recovery mechanisms, maintains consistency, considers accessibility, offers confirmation and review, educates users, and ensures mobile responsiveness.
Research
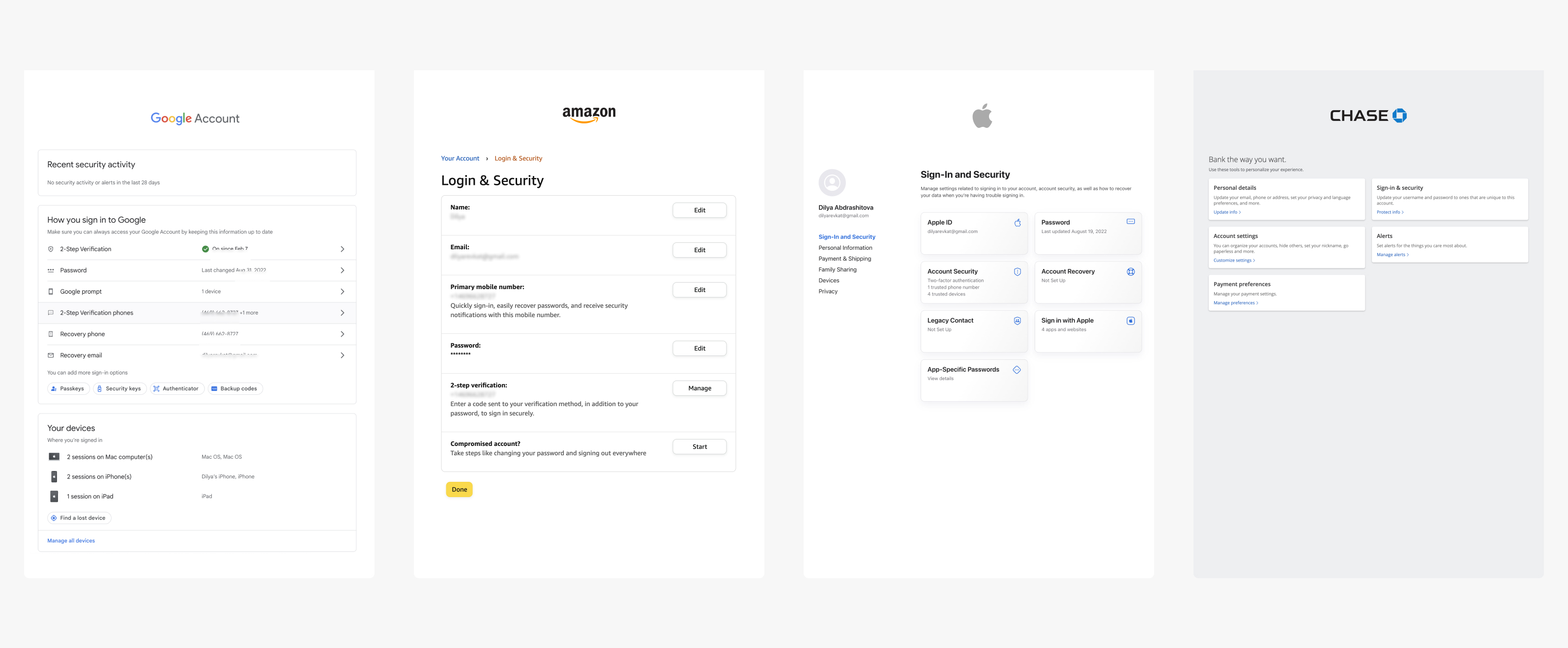
We conducted comprehensive qualitative and quantitative research, gathering valuable feedback on security from multiple platforms. Additionally, conducting user interviews allowed us to gain deep insights into the average user's understanding of security.
One of our most significant breakthroughs came during the ideation phase when we considered "Trusted Devices" and "Signed-In Devices" as separate sections. However, during competitive research, I signed into my bank account and discovered a recent sign-in from a "Microsoft PC" despite being a heavy Apple user. This discovery provided a crucial user insight – users are less concerned about whether a device is trusted or signed-in; instead, they want to ensure all devices on their profile are familiar to them. Consequently, if a user doesn't recognize a device and removes it, we should prompt them to update their sign-in information.
Solution
After an extensive ideation process, our team has arrived at an innovative and user-centric approach to enhance the security profile for our users. Recognizing the significance of managing security information effectively, we have adopted the principle of progressive disclosure. Our primary goal is to create a seamless and secure user experience without overwhelming them with excessive cognitive load.
To achieve this, we have broken down the security information into four distinct sections, each catering to specific aspects of the user's account:
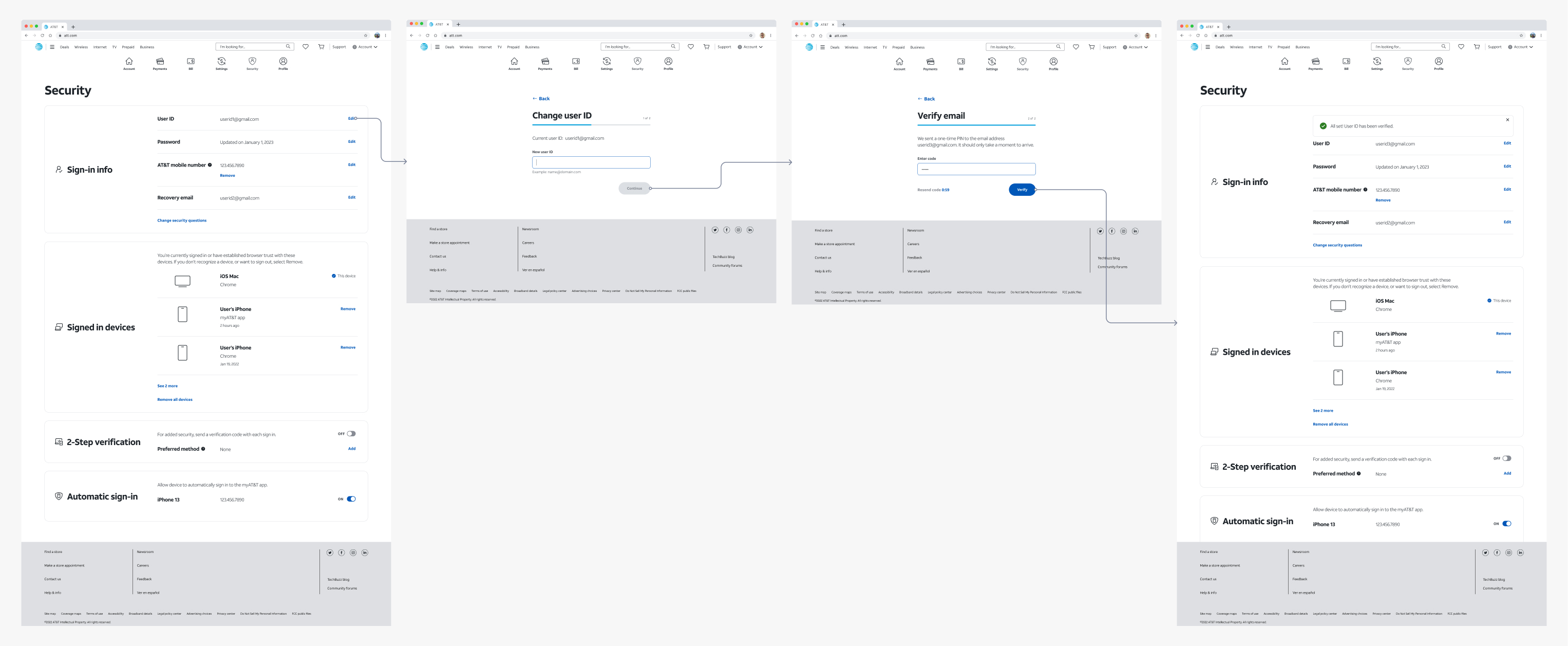
- Sign-in Info:This section covers the basic authentication process, ensuring that users have easy access to update and manage their sign-in credentials. By offering a straightforward interface, we empower users to modify their passwords, recovery options, and account email addresses with ease.
- Signed-in Devices:Knowing the importance of staying informed about account activity, this section provides users with a comprehensive overview of all devices and browsers currently logged into their account. In the event of any suspicious activity, users can quickly take action to secure their account by logging out unauthorized devices.
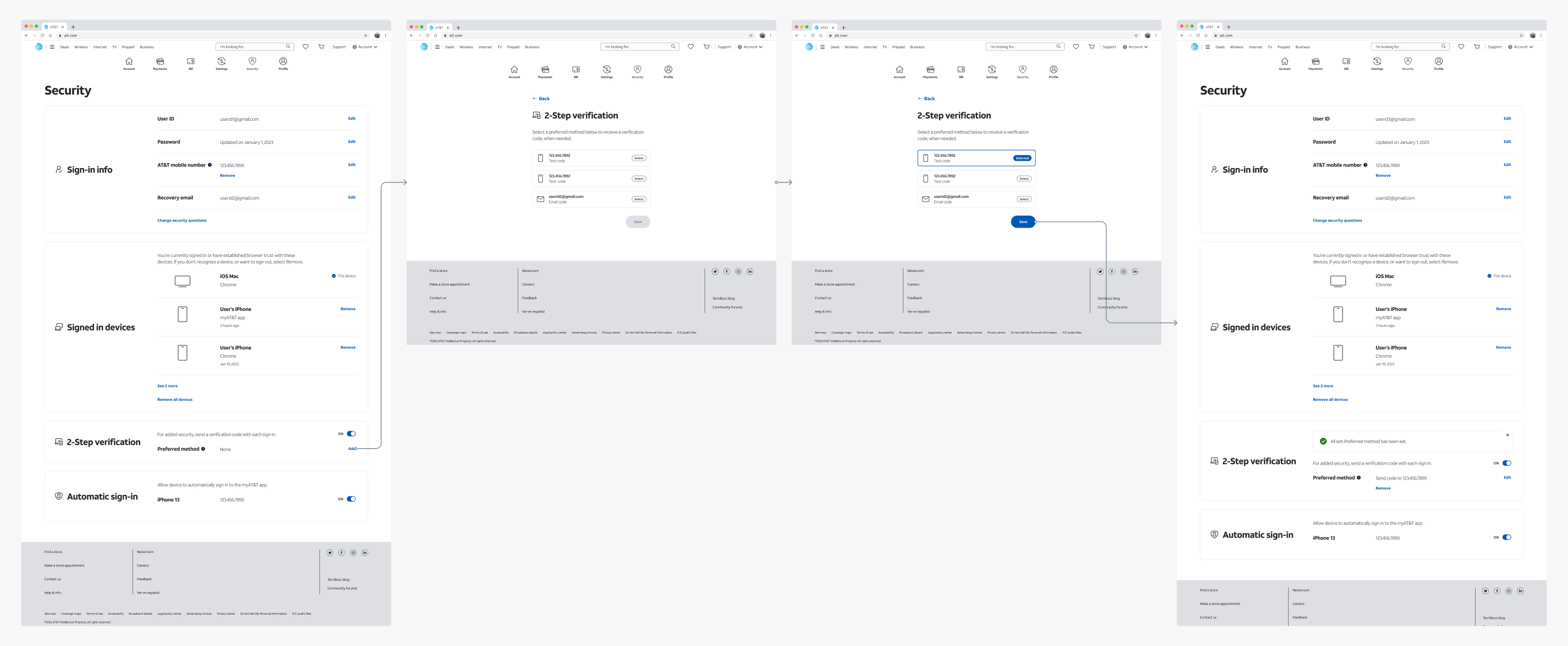
- 2-Step Verification:For users seeking an extra layer of protection, we offer advanced security settings through our 2-step verification feature. This powerful option allows users to safeguard their account even if their credentials are compromised. By integrating various authentication methods like authenticator apps, SMS, or physical security keys, we ensure a robust defense against unauthorized access.
- Automatic Sign-in:Our network-based authentication method streamlines the user experience further by automatically recognizing trusted devices and granting access without the need for repetitive sign-ins. This feature provides added convenience without compromising security, as it relies on the network environment to verify user identity.
By dividing the information into these easily accessible and comprehensible sections, we've created a user-friendly dashboard view. Users can effortlessly navigate through the different aspects of their security profile and take immediate action if any attention is required. This approach enables them to maintain control over their account security without feeling overwhelmed or confused.
In conclusion, our security profile solution takes a proactive approach to protect our users' accounts and sensitive information. With a focus on progressive disclosure and user-friendly design, we aim to elevate the standard of security while ensuring a smooth and hassle-free experience for all our valued users. Your peace of mind is our top priority.

Results
Our security profile solution yielded impressive outcomes:
- Reduced Incidents: 2-step verification thwarted unauthorized access, safeguarding against credential compromise.
- Increased Engagement: Users proactively managed security settings, updating info and reviewing devices.
- Improved Visibility: "Signed-in Devices" empowered users to monitor account activity in real-time.
- Streamlined Experience: "Automatic Sign-in" provided convenience without compromising security.
- Educating Users: Progressive disclosure enhanced security awareness and best practices adoption.
- Prompt Action: Immediate alerts ensured swift response to security issues.
- Positive Feedback: Users praised the user-friendly design and transparency.
Our solution effectively educates users, promoting strong security hygiene and a safer digital environment.